Did you know that October is cybersecurity awareness month?
Did you know that October is cybersecurity awareness month?
After all, there’s nothing spookier than the threat of a cybercriminal accessing your company’s sensitive data.
Cybercrime is on the rise. In 2021, the incidence of cyberattacks on corporate networks reached an all-time high, up 50% over the previous year. At this point, it’s no longer a question of if, but when your business will be affected by cybercrime.
If your company’s data is compromised, it could result in both a financial loss as well as a damaged reputation and loss of trust from customers and business partners alike. And once those relationships are damaged, it can be difficult to repair them.
In this day and age, cybersecurity needs to be a top priority for your business. Read on to learn more about the importance of cybersecurity, as well as cybersecurity tips for your company’s leadership, executive teams, and board members.
The Importance of Taking Cybersecurity Measures
 Cybersecurity protects your company’s data, including intellectual property, financial data, and the personally identifiable information of your customers, partners, and employees.
Cybersecurity protects your company’s data, including intellectual property, financial data, and the personally identifiable information of your customers, partners, and employees.
And contrary to what you might think, cybersecurity isn’t just an IT issue…it’s a board-level issue. If your company isn’t having discussions about cybersecurity at the board level, it’s time to start.
Your company leadership needs to be diligent in ensuring that your IT Department is keeping data secure and that cybersecurity measures are incorporated at every level of your company.
8 Cybersecurity Tips for Your Business
Incorporate these cybersecurity best practices to ensure your business is protected from cyber incidents and able to recover if you fall victim to one.
1. Educate Employees on Good Cyber Hygiene
 Training your staff on good cyber hygiene is a critical part of protecting your data. And it shouldn’t be a one-time thing…cybersecurity training needs to be ongoing.
Training your staff on good cyber hygiene is a critical part of protecting your data. And it shouldn’t be a one-time thing…cybersecurity training needs to be ongoing.
Incorporate cybersecurity training on a regular basis to ensure all employees are aware of potential threats and know how to keep themselves, their devices, and the data they work with secure.
Make sure your employees practice good cyber hygiene, beginning with smart password practices such as:
- Creating strong passwords
- Never sharing passwords
- Changing passwords regularly (monthly, ideally)
- Using two-factor authentication wherever possible
- Using password management software
Good cyber hygiene practices like these make it much more difficult for hackers to access your data.
2. Back Up Your Data
Always back up your data. Ideally, have your company data automatically backed up on a regular basis and stored off site. There are a couple of options for this, depending on your company’s size and budget.
One is to outsource your backups to a cloud-based provider that offers data backup as a service, such as these recommended by PC Magazine. The other option is to purchase data backup software designed for businesses.
Either option will require some investment. But keep in mind that not having your data backed up could prove to be much more expensive if you suffer a data breach at the hands of a hacker.
3. Guard Against Phishing Attacks and Ransomware
 Email security threats, such as phishing, ransomware, and business email compromise are among the most common forms of cyberattack. Hackers use these methods to pose as a legitimate individual or organization in order to gather sensitive information such as user names, passwords, and credit card details.
Email security threats, such as phishing, ransomware, and business email compromise are among the most common forms of cyberattack. Hackers use these methods to pose as a legitimate individual or organization in order to gather sensitive information such as user names, passwords, and credit card details.
Phishing is typically carried out via email. These messages direct recipients to enter their details into a fraudulent website that appears nearly identical to a legitimate one.
Never click on links in emails that come from untrusted sources, no matter how convincing they appear.
Ransomware hackers encrypt vital data on your company servers or devices, then demand payment before they will restore your access to the data.
Never pay a ransomware hacker. If you receive a ransomware message, contact authorities immediately.
Business Email Compromise, or BEC, is where hackers send an email that appears to come from a known source making a request that seems legitimate.
Rather than responding to these emails or clicking on any links they contain, contact the supposed sender of the email first to determine if it is legitimate or not…especially if the email is unsolicited or out of character.
4. Keep Your Devices Updated
 Make sure all company devices (computers, phones, printers…even smart appliances in the break room!) receive regular security updates. Proper software updates help patch vulnerabilities that could be taken advantage of by cybercriminals. And if your devices are all connected to a network, a vulnerability on one device could give hackers access to other connected devices.
Make sure all company devices (computers, phones, printers…even smart appliances in the break room!) receive regular security updates. Proper software updates help patch vulnerabilities that could be taken advantage of by cybercriminals. And if your devices are all connected to a network, a vulnerability on one device could give hackers access to other connected devices.
Also, make sure you have up-to-date anti-virus software installed on all applicable devices to provide an extra layer of protection.
Keep your data safe and your reputation secure by developing an effective, secure and profitable IT asset disposition (ITAD) program for your business! Our FREE GUIDE will show you how!
5. Maintain a Zero-Trust Approach
A zero-trust approach assumes that your network will be breached, and makes sure a hacker won’t get very far once they’ve gained access. This approach requires all users (both external and internal) to be authenticated and authorized before they can access company data.
A zero-trust approach should include the following practices:
- Give access to each user according to their needs—no more, no less.
- Review the background of all vendors.
- Know your vendors’ cybersecurity practices.
- Include security terms and standards in all vendor contracts.
- Audit third-party vendors.
6. Strengthen Your Risk Management Program
 Develop a plan to identify, assess, and respond to organizational risks, threats, and vulnerabilities. Perform routine vulnerability scans, ideally on a weekly or monthly basis. Then take action to shore up gaps in your security.
Develop a plan to identify, assess, and respond to organizational risks, threats, and vulnerabilities. Perform routine vulnerability scans, ideally on a weekly or monthly basis. Then take action to shore up gaps in your security.
You won’t be able to completely eliminate risk, and you may not have the budget or staff to address every risk.
To manage your risk most effectively, determine which vulnerabilities pose the highest risk to your organization. Once you identify the biggest threats, take action to mitigate those risks. Then if time and budget allow, move on to lower-risk threats.
7. Develop a Crisis Management Plan
A crisis management plan helps ensure company resilience if you do suffer a cyber attack. Create a plan to contain a data breach if it occurs, including a thorough business continuity plan and disaster recovery planning.
As part of this plan, be prepared to deal with the reputational fallout of a cyber attack. A data breach can severely damage your company’s reputation. It can break trust with clients, cause a dramatic decrease in your share prices, and lose you a lot of business.
Make sure you have a plan in place to address these issues after a cyber attack. Typically, the faster an organization responds in these situations, the better the outcome.
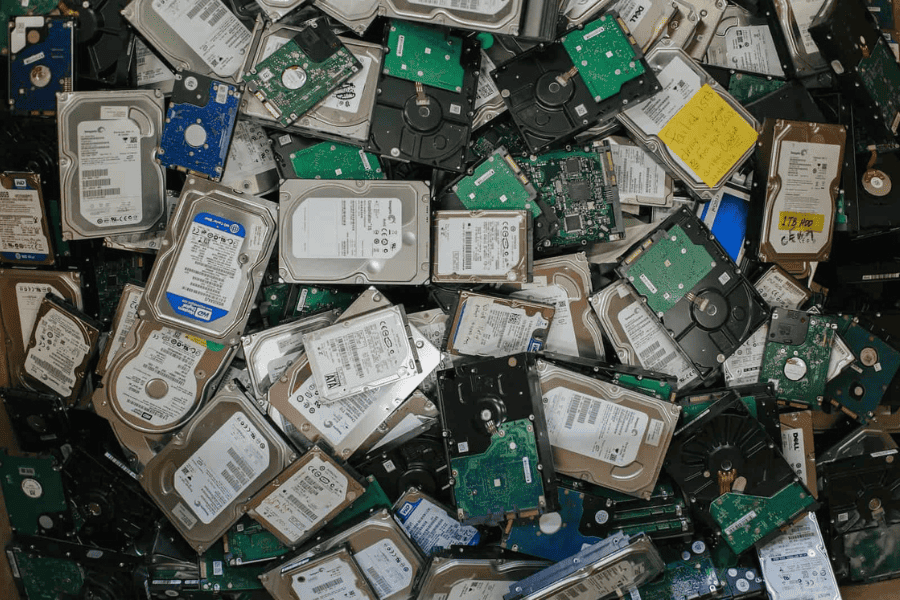
8. Invest in Certified ITAD Services
 ITAD (IT Asset Disposition) is a cybersecurity must-have. ITAD involves replacing old devices and disposing of them in a safe, environmentally-sound manner. This helps to ensure that any data that exists on old equipment is properly destroyed before the device is repaired or recycled properly.
ITAD (IT Asset Disposition) is a cybersecurity must-have. ITAD involves replacing old devices and disposing of them in a safe, environmentally-sound manner. This helps to ensure that any data that exists on old equipment is properly destroyed before the device is repaired or recycled properly.
Partnering with a reputable ITAD vendor like Repowered can help you avoid a costly and potentially devastating data breach.
We’ll customize an asset management plan that meets your corporate objectives and keeps your company fully compliant with applicable regulations. Our secure data sanitization and destruction process is continually tested and audited to guarantee that your data remains confidential and recycled components are processed responsibly.
We hope you found these cybersecurity tips helpful in keeping your organization safe from cybercriminals!
During this cybersecurity awareness month, take the time to improve your company’s protection against cybercrime by beginning an ITAD partnership with Repowered. Contact us at 763.432.3117 with any questions or to get started!
Recent News & Articles

Earth Day at Repowered: 4 Ways We’re Making a Difference for the Planet

Celebrating Juneteenth